OpSec 101 - Part II
VPNs
Table Of Contents
Recap
Disclaimer
VPNs Aren't About Security!
IP Address Threats
Geo-location Tracking
Browsing Behaviour
Fingerprinting
Download History
Data Breaches
VPN To The Rescue
Choosing A VPN Provider
Proton VPN
This Isn't The End
Recap
In the last OpSec article we talked about common threats, companies collecting "Telemetry" data, and what we can do to improve our privacy at the OS level by setting up Pop!_OS as our daily driver. Making our operating system more secure is a nice start, but there's still a lot more we can - and in my opinion should - do to limit our exposure. The next critical layer to tackle is network-level privacy.
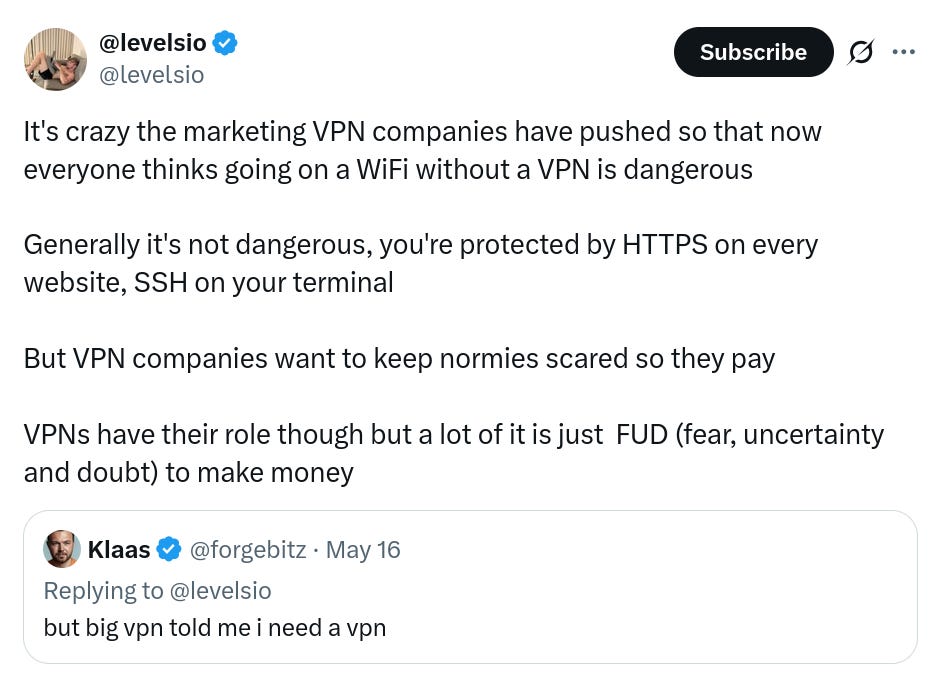
Recently, a discussion about VPN usage sparked quite some debate, with developers and privacy enthusiasts debating their effectiveness and necessity. I'm not trying to "dunk" on this or anything. There are good arguments for both sides in it. Like most privacy tools, VPNs come with their own set of tradeoffs. There will always be pros and cons for using a VPN. Ultimately, your choice should depend on your personal threat model and privacy requirements.
Since the thread highlighted several misconceptions about VPN usage, I'd like to share my perspective to help you make an informed decision.
Disclaimer
The information outlined during the writing of this may need to be modified in order to match updated software and services. Use the overall concepts as a guide. I encourage you to confirm all of my suggestions online before execution. There may be better ways of doing things today. Next, there is no perfect playbook for everyone. You do not need to replicate every step I take on behalf of myself. You may identify a better privacy plan for yourself than the specific examples presented here. And as always things written are not any type of advice. They are merely explicit examples of the actions I have taken. There will be a balance of enjoyable living and refusal to submit to the standard abuses of data collection. However, I won't sugar coat my opinions or offer less-secure options for the sake of convenience.
VPNs Aren't About Security!
As stated in the levelsio thread, VPNs don't offer (that much) security. There are some features that help enhance your networks overall security but the main purpose of using a VPN - at least for me - is to protect my data.
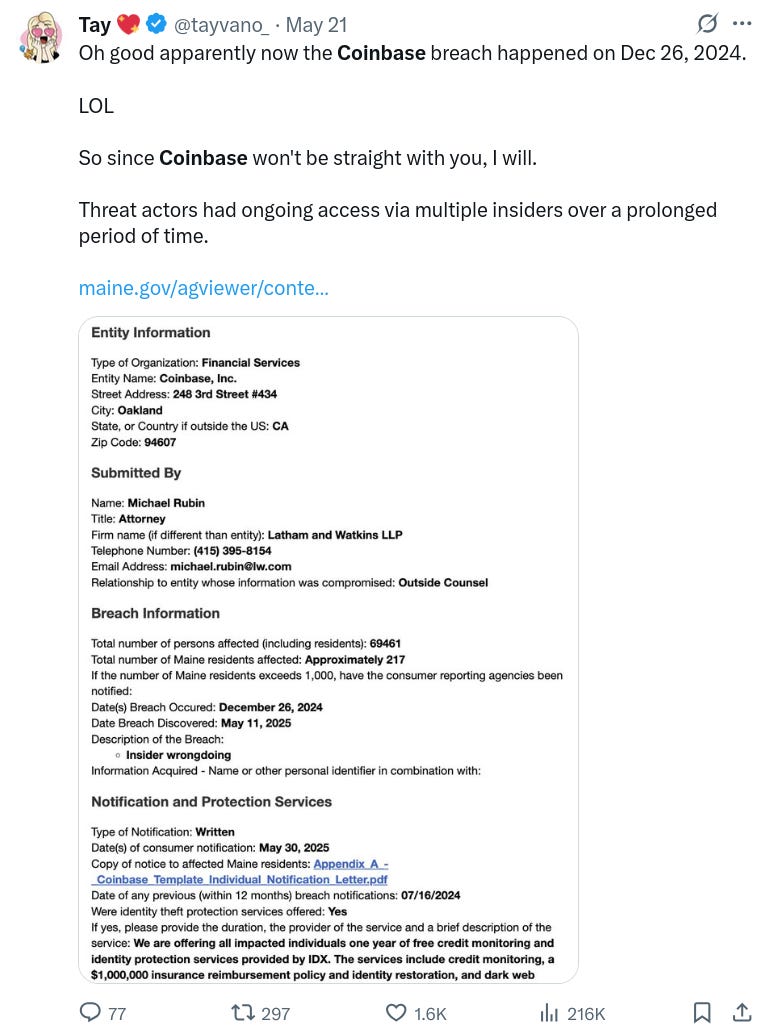
I've already talked about it in this article but to quickly reiterate: Your internet service provider (ISP) and every website you visit or service you use collects data about you and your behaviour with the purpose of selling it. All of these companies are notoriously bad at protecting your data! Their databases get breached by hackers daily and your data ends up being publicly available on the internet. And it's not just hackers. Employees getting blackmailed, bribed or generally acting in bad faith are nothing new as the recent Coinbase scandal demonstrated. Worse yet, companies often fail to notify users of breaches or actively lie to them about it.
IP Address Threats
This is especially concerning when it comes to your home IP address. This numeric value associates you and your internet browsing behavior to a unique identifier and can be used to document your location and track you through every website you visit. The more sites you visit, the worse it gets.
Some argue that there's no threat in sharing your IP address. I disagree! While it does not directly disclose your real-life home address (or geo-location in general), it has a number of threats associated with it:
Geo-location Tracking
First and foremost, it is relatively easy to pinpoint your physical location using just your IP address. Every website you visit gets your IP address. Every. Single. One. If just one of these countless services gets compromised or has a malicious employee, your location data is exposed.Law firms and other actors can simply request (or subpoena) this information. Even without considering legal methods, someone matching your identity to an IP address and then searching publicly available database dumps for more information about you, is a real threat!
To make things even worse, data brokers and advertising networks collect, aggregate, and sell IP-to-location mappings. Combined, this can create a detailed picture of your movements, locations and activities.
Browsing Behaviour
Your browsing history can be used against you in ways you might not expect.
It's true that HTTPS encryption protects the exact paths, query parameters and data sent of your web traffic. What this means is that your ISP can only see which domains you visited but nothing else. If you search for VPN review on google and end up on https://www.google.com/search?q=vpn+review, your ISP only sees that you visited
https://www.google.com
, but they know when and how often you visit each site.
This creates a detailed history of your online activities which can be obtained via court orders, exposed through data breaches or accessed by malicious employees. Your digital footprint can become a powerful tool that can be used against you, may it be professionally or personally. With ISPs keeping detailed logs of sites you visit, that footprint is a lot bigger than you might think.
Even worse, not all websites properly implement SSL/TLS protocols. When you visit these sites, your ISP can capture everything - including passwords, form data, and messages. This vulnerability opens the door for man-in-the-middle attacks (MITM), which we'll discuss in more detail later.
A very important note here: It's not only about your ISP. When connecting through public networks (cafés, airports, hotels), the one providing the connection can see the same things your ISP can! This creates a lot of ground for a broad range of MITM attacks.
Fingerprinting
Your IP address is just the tip of the iceberg when it comes to online tracking. Websites employ fingerprinting techniques that go far beyond simple IP address tracking.
When you visit a website, it can collect data about your:
Browser type and version
Operating system and configuration
Screen resolution and color depth
Installed fonts and plugins
Language settings
Time zone
Hardware capabilities
etc.
As highlighted in the discussion, these data points create a unique "fingerprint" that can identify you across websites. When combined with your home IP address, this creates an even more serious privacy risk - your online activities can be permanently tied to your physical location, making your digital footprint virtually impossible to separate from your real-world identity.
Download History
Your download history presents another significant privacy risk, especially when tied to your home IP address. Law firms have built entire business models around tracking IP addresses associated with unauthorized downloads, sending threatening legal notices, and demanding settlement payments (read: extortion).
Is someone else besides you using your connection from time to time? Can you be absolutely sure everything they do is within legal bounds? If you expose your true IP address, it's very easy for these law firms to issue subpoenas and fine you.
Data Breaches
Data breaches have become a daily occurrence. Companies' databases are constantly being leaked online, exposing user information. When these breaches happen, they don't just reveal your personal information - they can completely unravel your entire privacy setup.
This becomes especially problematic if you maintain separate online identities:
Creating anonymous accounts? They can be linked through your IP address.
Using different aliases? A data breach can connect them all.
Maintaining separate digital identities? Your home IP address becomes the common thread.
Even with careful compartmentalization, using your true IP address creates a permanent link between all your online activities. When (not if) a service gets breached, that single point of failure can collapse years of careful privacy work like a house of cards.
So if you believe any of this could remotely be a threat to you, you need to do something!
VPN To The Rescue
So how can a VPN help with all these threats? Virtual Private Networks (VPNs) route your traffic through their servers and encrypt all data between your device and their network. This creates several key benefits:
Reduced Attack Surface: Instead of exposing your true IP address to every website you visit, only your VPN provider knows it. The websites visited only see the IP address of your VPN provider. This significantly reduces the risk of your real location being exposed through data breaches or malicious actors.
Enhanced Privacy from ISPs: Your internet service provider can only see encrypted traffic to VPN servers - not which domains you visit or what you download. This prevents them from building detailed profiles of your browsing behavior.
Protection on Public Networks: When using WiFi at cafés, hotels, or airports, your traffic remains encrypted and secure from potential man-in-the-middle attacks.
Shared IP Addresses: Most VPN providers assign the same IP address to multiple users, making it much harder to track individual activity. Even if a website fingerprints this IP address, it can't be uniquely tied to you.
Reputable VPN companies utilize "no logging" policies, which means they don't store any information about what sites you visited. This makes tracing your online activity much much harder.
However, it's crucial to understand that VPNs aren't an ultimate solution. While they help protect against IP address-based tracking, they won't prevent browser fingerprinting or other advanced tracking methods. This is why browser hardening and additional privacy tools are crucial parts of a comprehensive security setup (more on this later).
Choosing A VPN Provider
First of all: Ignore all VPN review sites. These are typically owned by VPN companies themselves, which explains why their top 10 lists look awfully similar.
Unfortunately, VPN providers are also notoriously bad at protecting your data. They often get caught selling it just like ISPs. They lie about having "no logging" policies when in reality they store data about your behaviour, making it possible to trace everything back to you.
It's crucial to very carefully consider any of the following critical factors when choosing a VPN provider:
Trust and Transparency: Look for providers that undergo regular third-party audits. Choose companies based in jurisdictions with strong privacy laws. I'd rather rely on a swiss company to protect my privacy than a russian or chinese one. Prefer independently owned companies over those under large corporate umbrellas. Big brands can just spin up new skins of their failed products and start new marketing campaigns when their users bail. Independently owned ones have a lot more to lose reputation wise.Verify their no-logging claims through audit reports
Logging Policy: Understand that absolute zero logging is technically impossible. What matters is that any necessary logs are: a) only kept during your active connection, b) automatically purged after disconnection, c) not accessible in a way that could identify you
Business Model: Avoid free VPN services - they often monetize through data collection. Look for clear revenue sources (i.e., subscription payments). Remember: If the service is free, you are likely the product
Technical Infrastructure: Prefer providers with large user bases sharing IP addresses to blend in with the crowd. This makes fingerprinting significantly harder.Look for open-source clients that can be audited by the community. Regular third party audits ensure that this open-source code and nothing else is being used to provide you service.Consider server ownership and control mechanisms
Payment Privacy: Look for providers accepting anonymous payment methods. Consider cryptocurrency or cash payment options. Understand that you're not staying anonymous but simply protect your banking details here
Self-Hosting Considerations: While offering more control, self-hosted VPNs have limitations. Single IP addresses makes you more identifiable. Self-hosting requires significant technical expertise since you become responsible for security.
Important Note: I believe that all VPNs are flawed. No provider is perfect. Every company relies on rented servers worldwide, potentially outside their direct control. However, this doesn't mean VPNs are useless - they're simply one layer in a broader privacy strategy. Without a VPN your ISP and any site you visit have a much easier time collecting and aggregating your data. I simply choose the provider that has the most to lose from betraying my trust and has a proven track record of protecting theirs users privacy.
Yet another note: If your government or another sufficiently empowered actor with enough resources puts their scope on you, choosing the perfect jurisdiction or VPN provider won't save you. My biggest threat aren't governments though. For me it's all about data breaches and aggregation techniques of ISPs and websites.
Proton VPN
After careful consideration of all these factors, I personally use and recommend Proton VPN. Here's why:
They have a proven track record! There are no documented cases of user data exposure. They are open-source and regularly audited by a third-party, which they share publicly.
Proton has a transparent no-logs policy, see here about the details.. Their no-logging policy also gets regularly audited.
As a swiss company, their privacy practices are based on one of the best privacy laws around the world. They typically only respond to swiss court orders.
Privacy-first payment options like BTC or anonymous cash via mail without personal information are supported.
I trust Proton VPN more than the majority of VPN companies out there.
You can see their pricing here. Their VPN Plus option is enough for most people.
I received no compensation for this article beyond potential referral commissions and I am not affiliated with Proton VPN at this point.
This Isn't The End
While setting up a VPN is a crucial step toward better privacy, it's just one piece of a much larger puzzle. In the upcoming OpSec articles, we'll explore how to build a comprehensive privacy setup that goes far beyond just using a VPN.
We'll have a look at a proper VPN configuration - from choosing consistent geo-locations over preventing account restrictions, to implementing kill-switches that prevent data leaks during disconnects. We'll discuss hardware 2FA implementation, dedicated IP adress considerations to mitigate VPN blocks by streaming services and such, and proper log management to ensure your VPN provides maximum protection without losing the ability to actually use your internet connection in a normal way.
Next, we'll tackle some more network-level protection. This includes setting up a custom hardware firewall that integrates with your VPN, implementing protection against VPN crashes and disconnects, while also establishing network-wide privacy for all your devices. We'll also dive into DNS blocking and filtering to further reduce tracking.
The browser, being your main interface to the internet, deserves special attention too. We'll cover recommended browsers, essential privacy-enhancing extensions, and techniques to protect against fingerprinting. You'll learn how to properly manage cookies, cache, and other potential privacy leaks.
Remember: There is no single privacy tool that will magically protect you. Privacy is achieved through carefully selected tools, proper configuration, regular maintenance, and most importantly - mindful online behavior. Each solution comes with its own tradeoffs, and what works for one person might not work for another.
Combined with our previous guide on OS-level privacy, you now have a solid foundation: a custom OS that respects your privacy and a VPN to protect your network traffic. But there's much more to come.
So long, stay safe!